Bitcoin Private Key Jwt images are ready. Bitcoin Private Key Jwt are a topic that is being searched for and liked by netizens now. You can Find and Download the Bitcoin Private Key Jwt files here. Get all free vectors.
If you’re searching for Bitcoin Private Key Jwt pictures information linked to the Bitcoin Private Key Jwt interest, you have visit the right blog. Our site always provides you with hints for seeking the maximum quality video and picture content, please kindly surf and locate more enlightening video articles and images that fit your interests.
Bitcoin Private Key Jwt. ES256K JWK curve name. HS256 for HMAC SHA-256 or RS256 for RSA SHA-256RS256 is recommended because it uses asymmetric publicprivate keys instead of relying on a shared private key. The private key is essentially a shared secret between you and Vonage. 64-bit 128-bit 256-bit 512-bit 1024-bit 2048-bit 4096-bit.
 Pin On Consumer Research From pinterest.com
Pin On Consumer Research From pinterest.com
The input can be either text or HEX according to your preference. JWTs are created with a private key but the key isnt included in the payload. HS256 for HMAC SHA-256 or RS256 for RSA SHA-256RS256 is recommended because it uses asymmetric publicprivate keys instead of relying on a shared private key. The JWT isnt signed using an asymmetric cipher like RSA. It is known to be secure because the JWT can be signed using a secret or publicprivate key. Support for EC DSA signatures on the secp256k1 curve which is used in Bitcoin and Ethereum was added in version 59 of the Nimbus JOSEJWT library.
ES256K JWK curve name.
So I have to get how to get security key object from the key value. Dean Apr 6 19 at 845. What I want to achieve is that I want to use RS512 to encode JWT token from a private key. It can not be stressed enough but JWT heavily relies on the private key to stay absolutely private. The idea behind it is simple. Base58 Encoder - Converts either text or HEX to Base58.
 Source: nabenik.com
Source: nabenik.com
How to generate an EC key pair on the. The idea behind it is simple. JSON Web TokensJWT is a way of representing claims securely between two parties. It is known to be secure because the JWT can be signed using a secret or publicprivate key. How to generate an EC key pair on the.
 Source: devglan.com
Source: devglan.com
Public Key Please update your settings- public-key page with this public key. The private key is essentially a shared secret between you and Vonage. The idea behind it is simple. JSON Web Token JWT with ES256K secp256k1 signature. How to generate an EC key pair on the.
 Source: br.pinterest.com
Source: br.pinterest.com
Support for EC DSA signatures on the secp256k1 curve which is used in Bitcoin and Ethereum was added in version 59 of the Nimbus JOSEJWT library. We can use ECDSA publicprivate key pair to sign JWT as official. A very common use of a JWT token is an API authentication mechanism. JSON Web TokensJWT is a way of representing claims securely between two parties. Public Key Please update your settings- public-key page with this public key.

As you stated I can also add any other claim and you system has no choice but trust it as I was able to create a valid signature. We can use ECDSA publicprivate key pair to sign JWT as official. It is known to be secure because the JWT can be signed using a secret or publicprivate key. HS256 for HMAC SHA-256 or RS256 for RSA SHA-256RS256 is recommended because it uses asymmetric publicprivate keys instead of relying on a shared private key. The third and final section in the jwtio debugger is the signature.
 Source: pinterest.com
Source: pinterest.com
I think I used wrong security format. Base58 Encoder Decoder is a free online developer tool to encode either text or HEX to Base58 or decode Base58 to text or HEX. 1639248876 Genarate private key const privateKey ECDSA. In the event that you are sure that your old wallet cannot be recovered by a third party For instance the software has been removed or your paper wallet has been lost you may just proceed by importing your private key into your new wallet. Secp256k1 The ES256K algorithm for JOSE is specified in COSE and JOSE Registrations for WebAuthn Algorithms.
 Source: dzone.com
Source: dzone.com
The first section is known as the headerThis is where a few key pieces of information are contained. A very common use of a JWT token is an API authentication mechanism. It uses a HMAC which uses a single secret key. The exception does not make sense. It is known to be secure because the JWT can be signed using a secret or publicprivate key.
 Source: stackoverflow.com
Source: stackoverflow.com
HS256 for HMAC SHA-256 or RS256 for RSA SHA-256RS256 is recommended because it uses asymmetric publicprivate keys instead of relying on a shared private key. Failure to only ever use a nonce value once makes the private key easily recoverable and this has been seen in the wild with both Sonys Playstation 3 and Bitcoin. The private key is essentially a shared secret between you and Vonage. This tool is split into two modes. Support for EC DSA signatures on the secp256k1 curve which is used in Bitcoin and Ethereum was added in version 59 of the Nimbus JOSEJWT library.
 Source: in.pinterest.com
Source: in.pinterest.com
The input can be either text or HEX according to your preference. A very common use of a JWT token is an API authentication mechanism. It is known to be secure because the JWT can be signed using a secret or publicprivate key. JWTs are created with a private key but the key isnt included in the payload. How to generate an EC key pair on the.
 Source: pinterest.com
Source: pinterest.com
It uses a HMAC which uses a single secret key. What I want to achieve is that I want to use RS512 to encode JWT token from a private key. Can not use secp256k1 which is famous for Bitcoin. 1639248876 Genarate private key const privateKey ECDSA. So I have to get how to get security key object from the key value.
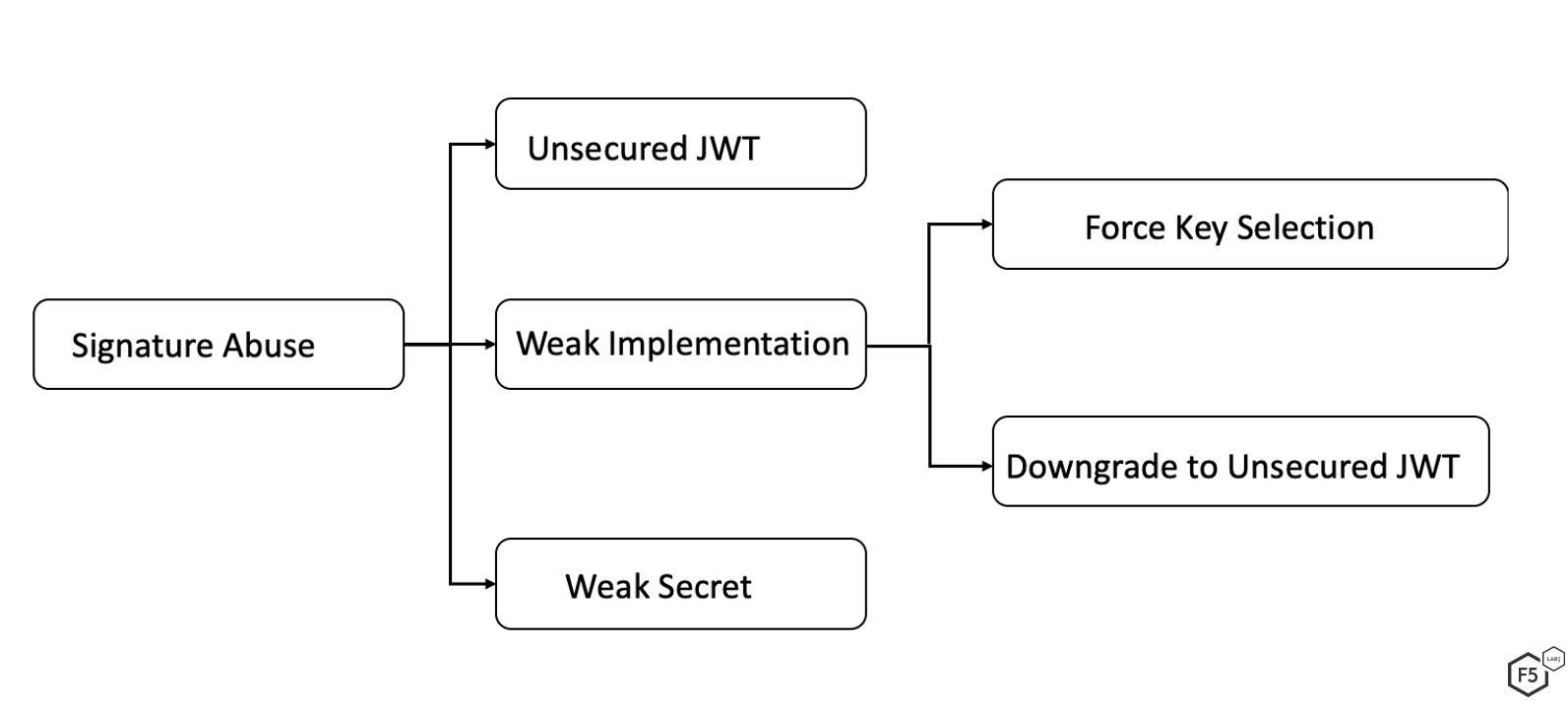 Source: f5.com
Source: f5.com
Dean Apr 6 19 at 845. You can set it via the input type option. Indeed the point here is not to prove to someone else that you signed the token. The third and final section in the jwtio debugger is the signature. We can use ECDSA publicprivate key pair to sign JWT as official.
 Source: stackoverflow.com
Source: stackoverflow.com
The private key is essentially a shared secret between you and Vonage. Indeed the point here is not to prove to someone else that you signed the token. The idea behind it is simple. Failure to only ever use a nonce value once makes the private key easily recoverable and this has been seen in the wild with both Sonys Playstation 3 and Bitcoin. The private key is essentially a shared secret between you and Vonage.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title Bitcoin Private Key Jwt by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.





